IPsec Site-to-site VPN tutorial
In this article, I want to introduce about the use of IPsec Site-to-site VPN, why we should use and how to configure it.
Nowadays, many companies and corporations have their branch offices far away from its headquarters but they need to communicate as if they were in a LAN. This is the place where site-to-site VPN comes into play. Site-to-site VPNs connect entire networks to each other, for example, they can connect a branch office network to a company headquarters network. In the past, a leased line or Frame Relay connection was required to connect sites, but because most corporations now have Internet access, these connections can be replaced with site-to-site VPNs.
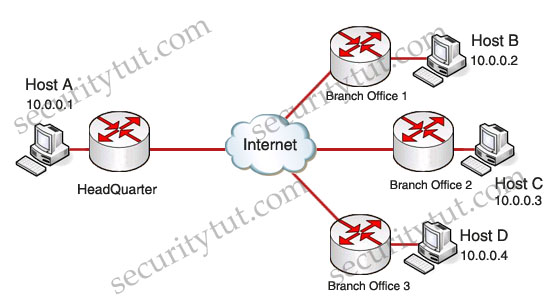
Organizations use virtual private networks (VPNs) to create an end-to-end private network connection (tunnel) over third-party networks such as the Internet or extranets. The tunnel eliminates the distance barrier and enables remote users to access central site network resources. However, VPNs cannot guarantee that the information remains secure while traversing the tunnel. For this reason, modern cryptographic methods are applied to VPNs to establish secure, end-to-end, private network connections.
The IP Security (IPsec) protocol provides a framework for configuring secure VPNs and is commonly deployed over the Internet to connect branch offices, remote employees, and business partners. It is a reliable way to maintain communication privacy while streamlining operations, reducing costs, and allowing flexible network administration.
IPSec VPN negotiation can be broken down into five steps
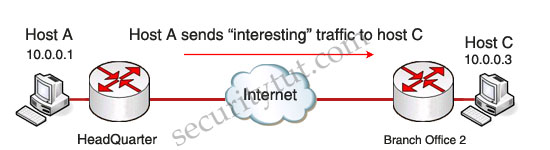
Step 1. An IPsec tunnel is initiated when Host A sends “interesting” traffic to Host B. Traffic is considered interesting when it travels between the IPsec peers and meets the criteria that is defined in the crypto access control list (ACL).
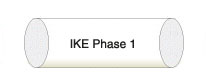
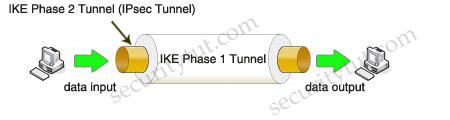
Step 2. Router1 and Router2 negotiate a Security Association (SA) used to form an IKE Phase 1 tunnel, which is also known as an ISAKMP tunnel.
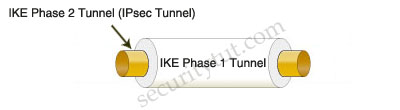
Step 3. Within the protection of the IKE Phase 1 tunnel, an IKE Phase 2 tunnel is negotiated and set up. An IKE Phase 2 tunnel is also known as an IPsec tunnel.
Step 4. After the IPsec tunnel is established, interesting traffic flows through the protected IPsec tunnel
Step 5. After no interesting traffic has been seen for a specified amount of time, or if the IPsec SA is deleted, the IPsec tunnel is torn down.
Elements of a site-to-site VPN:
+ Headend VPN device: Acts as a VPN termination device, located at a primary network location (for example, a headquarters location)
+ VPN access device: Serves as a VPN termination device, located at a remote office
+ Tunnel: Provides a logical connection over which traffic flows (for example, an IP Security [IPsec] tunnel and/or a Generic Router Encapsulation [GRE] tunnel)
+ Broadband service: Transports traffic to and from the Internet (for example, over a cable or DSL connection)
Now you understand the fundamental of IPsec site-to-site VPN. In summary, the site-to-site VPN requires Internet or other common environments as the transport so security is the primary concern and this can be protected by IPsec. IPsec operates at Layer 3 of the OSI model (Network layer) and it is independant of the applications. It means that the applications don’t require any modifications to use IPsec.
IPsec Modes
IPsec uses 2 modes to establish a secure communication channel between network nodes, Transport mode & Tunnel mode. These 2 modes are different in what parts of IP headers and payloads are to be kept confidential. In Transport mode, security is provided only for the transport layer and above while Tunnel mode will encapsulate the original IP header and creates a new IP header that is sent unencrypted across the untrusted network. We will not go deeper in these modes to keep this tutorial simple.
IPsec Transforms
IPsec delivers data confidentiality services by executing a “transform” on plain text data into a block of ciphertext. Common ciphers used in the IPsec transforms are DES, 3DES, and AES. 3DES and AES are considered to be stronger encryption ciphers than DES, as they use longer encryption keys (128-bit key for 3DES and 256-bit key for AES).
Note:
Confidentiality ensures that only authorized individuals can view sensitive data. Powerful methods of ensuring confidentiality are encryption and access controls.
Integrity ensures that data has not been changed by an unauthorized individual.
Availability ensures that access to the data is uninterrupted. Denial-of-service (DoS) attacks attempt to compromise data availability. These attacks typically try to fail a system using an unexpected condition or input, or fail an entire network with a large quantity of information.


