Identity Services Engine
|
Quick Summary Cisco ISE is the centralized AAA and policy engine solution from Cisco. Cisco ISE integrates with numerous Cisco products and third-party solutions to allow you to maintain visibility of who and what is accessing your network, and to enforce access control consistently. Posture is a service in Cisco Identity Services Engine (Cisco ISE) that allows you to check the compliance, also known as posture, of endpoints, before allowing them to connect to your network. RADIUS Change of Authorization (CoA) is a feature that allows a RADIUS server to adjust an active client session. For instance, ISE can issue the CoA RADIUS attribute to an access device to force the session to be reauthenticated (change the AAA attributes of a session after it is authenticated). |
Question 1
Question 2
Question 3
Question 4
Question 5
Explanation
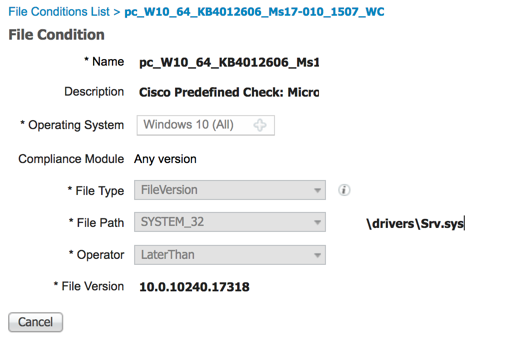
A posture policy is a collection of posture requirements, which are associated with one or more identity groups, and operating systems. We can configure ISE to check for the Windows patch at Work Centers > Posture > Posture Elements > Conditions > File.
In this example, we are going to use the predefined file check to ensure that our Windows 10 clients have the critical security patch installed to prevent the Wanna Cry malware.
Question 6
Explanation
The Cisco ASA Version 9.2.1 supports RADIUS Change of Authorization (CoA) (RFC 5176). This allows for posturing of VPN users against the Cisco ISE without the need for an IPN.
Question 7
Question 8
Question 9
Explanation
Posture is a service in Cisco Identity Services Engine (Cisco ISE) that allows you to check the state, also known as posture, of all the endpoints that are connecting to a network for compliance with corporate security policies.
A posture policy is a collection of posture requirements that are associated with one or more identity groups and operating systems.
Posture-policy requirements can be set to mandatory, optional, or audit types in posture policies.
+ If a mandatory requirement fails, the user will be moved to Non-Compliant state
+ If an optional requirement fails, the user is allowed to skip the specified optional requirements and the user is moved to Compliant state
This question did not clearly specify the type of posture policy requirement (mandatory or optional) is not met so the user can be in Non-compliant or compliant state. But “noncompliant” is the best answer here.
Question 10



Question 10 correct should be B.
Q10: is the answer not B. it asks about benefits of compliance.
Any explanation on question 10?
Question 10: correct should be B
802.1x is performed before the compliant posture, so it cannot be a benefit.
“Posture run-time services begin with the Discovery Phase. An endpoint session is created after the endpoint passes 802.1x authentication. The client agent then attempts to connect to a Cisco ISE node by sending discovery packets through different methods”
Q10: B
The question is about the benefits policy posturing.
I could go either way on this one. A or B there is merit depending on how you interoperate what is a benefit.
Simply because microsoft has performed the latest update, doesnt mean that the company wants to have it installed. That will depend on the posture policy and maybe your policy is simply asking for an antivirus and firewall enabled.
A is not 100% clear but if I had to choose one, I would go for A. simply by doing an elimination process from the 4 of them
Q10.
ISE allows to check a specific MS patch, but not the “latest” one.
The answer should be D. “It allows CoA to be applied if the endpoint status is compliant”.
It refers us to the procedure of endpoint assessment. Initilay the status is “unknown”, further if it is “compliant”, ISE does CoA.
@Admin
I agree with Ivan re Q.10
The question can be re-phrased for a better clarity to “what is the benefit the endpoint will get if its posture changes from non-compliant to compliant?”
For me the answer is obvious, that it will change the authorization level from limited access to full access.
So, I believe the best answer is
D. It allows CoA to be applied if the endpoint status is compliant.
Please review ….
Q8
answers are A & C
Check below link, and check the section where ####
https://www.cisco.com/c/en/us/td/docs/security/ise/2-2/admin_guide/b_ise_admin_guide_22/b_ise_admin_guide_22_chapter_010111.html#concept_46207D0DFA4341D9981898C668C2C737
Posture Conditions
A posture condition can be any one of the following simple conditions: a file, a registry, an application, a ####service#####, or a dictionary condition. One or more conditions from these simple conditions form a compound condition, which can be associated to a posture requirement.
When you deploy Cisco ISE on your network for the first time, you can download posture updates from the web. This process is called the initial posture update.
After an initial posture update, Cisco ISE also creates Cisco defined simple and compound conditions. Cisco defined simple conditions have pc_ as their prefixes and compound conditions have pr_ as their prefixes.
You can also configure Cisco ISE to download the Cisco-defined conditions periodically as a result of dynamic posture updates through the web. You cannot delete or edit Cisco defined posture conditions.
A### user defined condition#### or a Cisco defined condition includes both simple conditions and compound conditions.
Agree with @Ivan, best answer seems D to me:
A. It allows the endpoint to authenticate with 802.1x or MAB. -> This is before posture policy.
B. It verifies that the endpoint has the latest Microsoft security patches installed. -> This the posture policy itself.
C. It adds endpoints to identity groups dynamically. -> This would happen after the posture assesment. This applies to TrustSec, but we don’t know if it is configured.
D. It allows CoA to be applied if the endpoint status is compliant. -> This happens after the the posture assesment finished, when moving the status from “unknown” to “compliant”.
@NetEng, I think that “user defined condition” refers to conditions that administrator can configure on Cisco ISE, not the checks a condition can do.
In the same document you can see a list of simple conditions that you can use:
File Condition Settings
Registry Condition Settings
Application Condition Settings
Service Condition Settings
Dictionary Simple Condition Settings
USB Condition Settings
Q10 I think is B
Q10 to my understanding – the device will be checked for posture assessment depending on the policy configured in ISE. Once the policy checks matches the user is allowed into the network. That is the benefit of being compliant.
It makes no sense to join the network and then check for compliant… the user can easily do reconnaissance of the network once connected for few seconds also..
@Admin
Why you still think that the Q10 is A?
@all: Thanks for your information, we updated Q10!
where did you find the questions?
are those the only Q . for SISE 300-715?
May i know if you have ISE dump?
Hi all,
Question 10- which is the answer?
Answer for Q 10?
Hello, earlier you used to have details on every topic and explanations and then questions were easy to understand for example in 9tut but my question is why don’t we have explanations here on securitytut even with premium membership?
@WA: We also have explanation on this site but this topic is rather basic so we did not explain much.
I bet A. Posture takes place before authentication. If a device is not compliant, ISE doesn’t allow to authenticate.
what is the ise exam domain of this tut ?